Github: https://github.com/WardPearce/Purplix.io
View our canary: https://purplix.io/c/purplix.io/3ZjhTlZRWv8iqa6sn9yJ3TRiIkVbwITOOlwLjJD36jQ
What is Purplix Canary?
Purplix Canary is a free & open source warrant canary tool what helps you to build trust with your users.
It allows you to inform users cryptographically if your site has been compromised, seized or raided by anyone.
How does it work?
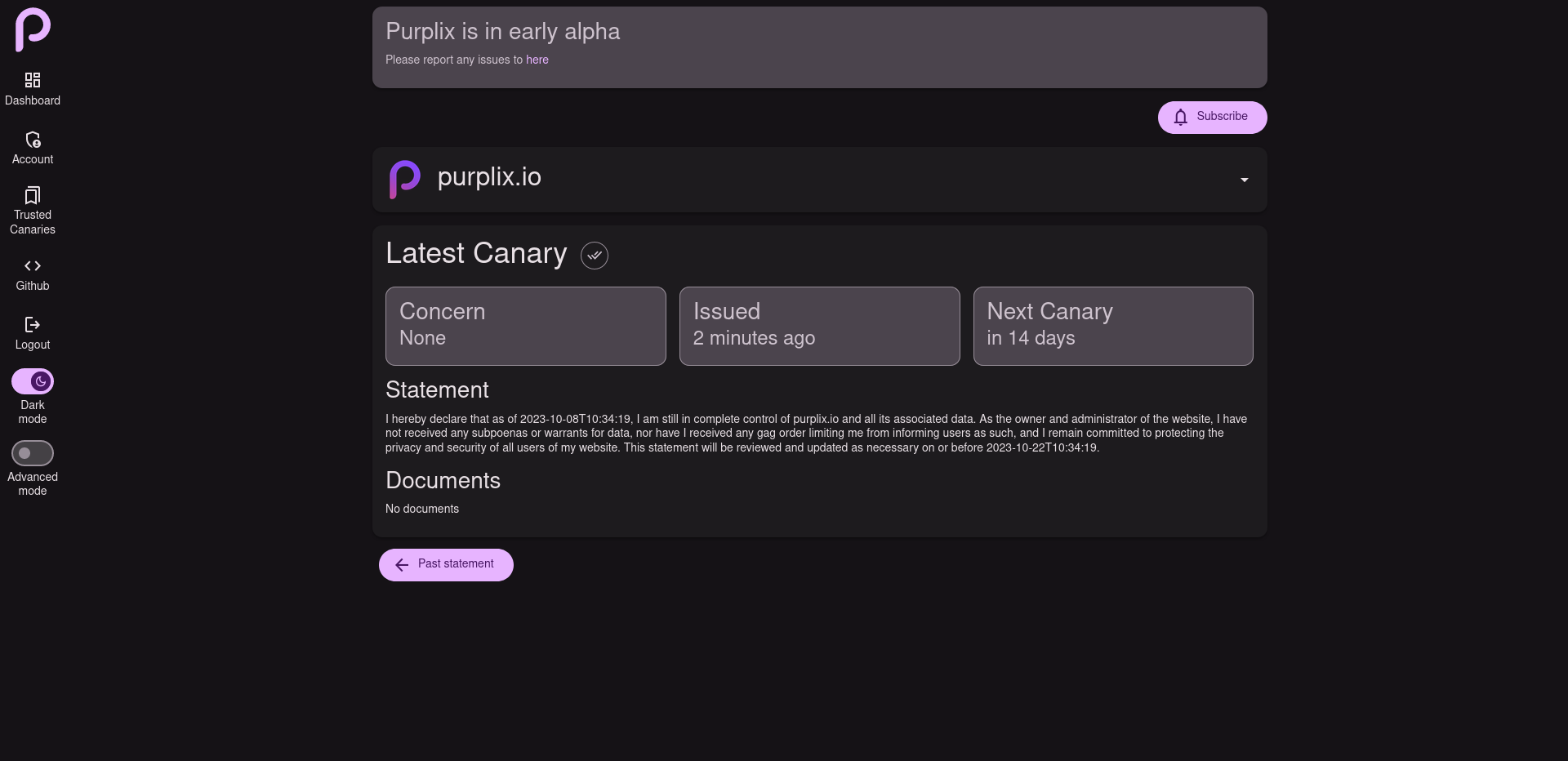
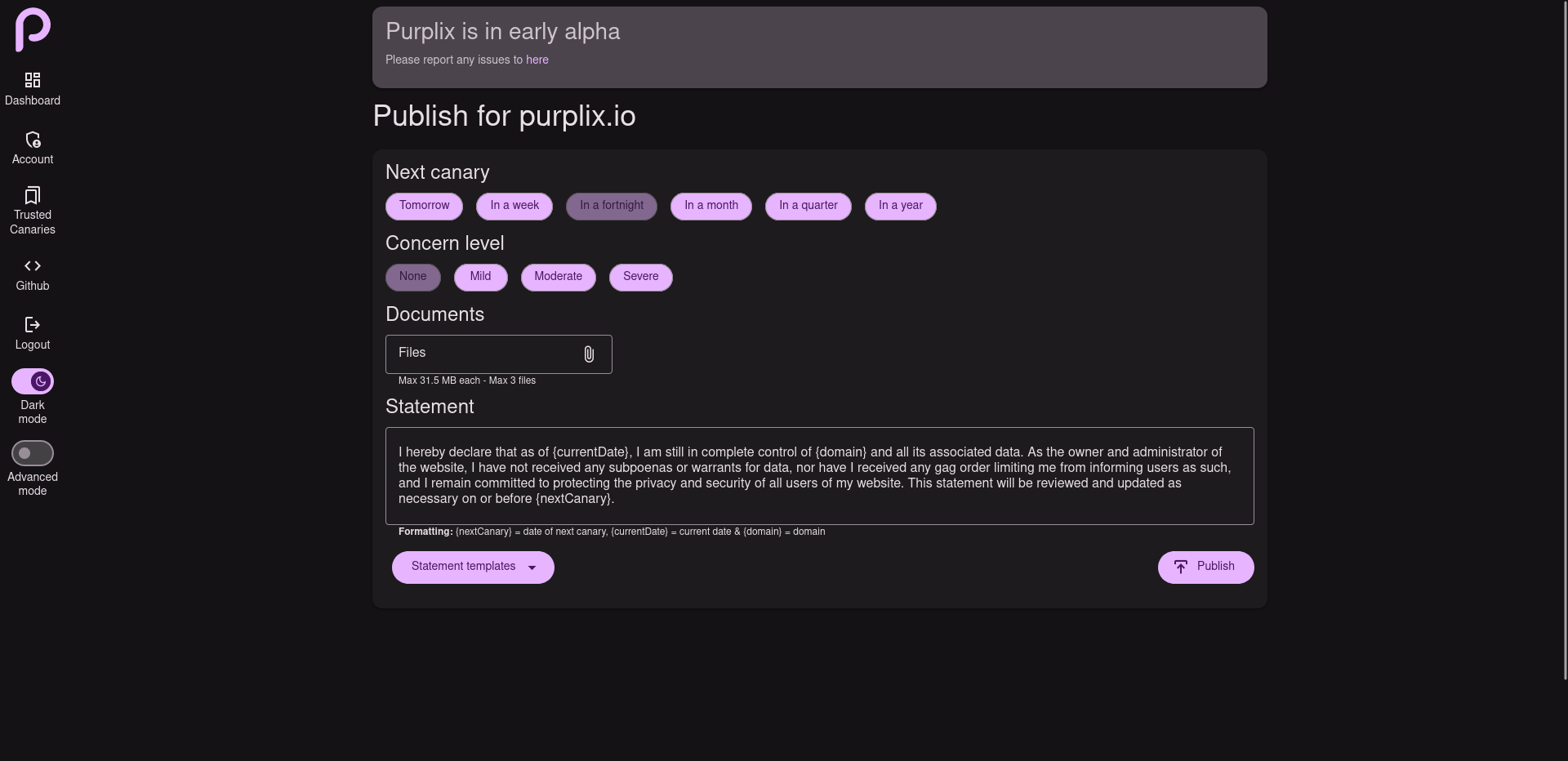
Site verification
Purplix uses DNS records to verify the domain the canary is for, giving your users confidence they are trusting the right people.
Canary signatures
Each domain is associated with a unique key pair. The private key is generated locally and securely stored within the owner’s keychain. When a user visits a canary from a specific domain for the first time, their private key is used to sign the public key. This signed version of the public key is then automatically employed for subsequent visits, effectively mitigating man-in-the-middle attacks and ensuring the trustworthiness of canary statements from the respective domain.
Files
Canaries can include signed documents to help users further understand a situation.
Notifications
Users are automatically notified on the event of a new statement being published.



Someone please correct me if I am wrong, but I was under the impression that warrent canaries were a broken concept. Anyone with the power to submit a warrant to a company also has the ability to prevent the company from triggering their canary.
The idea is that there is no such action as “triggering the canary” that the government can stop them from taking. Instead they refrain from updating it, thus alerting people that something has occurred. However, since the point of a canary is that not updating it raises concerns, I’m not sure how this service makes any sense (alerts on new canaries?).
The idea is that there is a big difference between the government saying “don’t tell anyone about this” and saying “you must make a false statement (the canary) every X amount of time indefinitely.” In the past courts in the US have taken a fairly dim view of the government trying to compel speech. There are some example cases at https://en.m.wikipedia.org/wiki/Compelled_speech#United_States.
None of those compelled speech examples include national security though, which has its own level of rules and courts. (I am not American or a lawyer, so i may be wrong).
And if a company can be compelled to hand over customer data, why wouldnt they be hand over access to the systems that update the canaries?
The other issue is thar once a canary is triggered, it cant be reset, which means that XXX agency can trigger the canary with something meaningless, and then its forever untrustworthy.
You may well be correct, and they are sufficient, but i am not convinced that canaries work, especially against the higher level adversaries.
Yes, most of those points are the concerns with warrant canaries. So far as we know the concept is totally untested in court so it’s hard to say what the result would be until it happens.
Updating the canary should require a human input (like a password to unlock the GPG key), which is not sometime the government would generally get access to (they make a request for data about XYZ user, and the company turns it over; they wouldn’t get actual access to the production system). The government could seek a ruling to force the company to update the canary, but as such a thing hasn’t been granted before (at least as far as we know), it’s not a guarantee. So, there is a chance that the warrant canary will serve to alert users to something happening, which is better than nothing. But because of its untested nature, it might be broken by a court.
I’m not sure I understand your point about “once it’s triggered it can’t be reset.” If a company fails to update their canary on schedule it means something happened that they can’t disclose. Once they are released from the NDA they can release a new canary explaining what happened.
Wikipedia does claim that patriot act subpeonas can penalise any disclosure of the subpeona. But i am not a lawyer, and afaik this is untested (or at least undisclosed :/ )
https://en.m.wikipedia.org/wiki/Warrant_canary
I think my point is that a gag order with a long time out essentially kills the canary, even if it doesnt affect the vast majority of the services users.
Thanks for your response though, I appreciate the additional information.
I wonder where mandated sonograms and abortions are bad disclaimers to patients seeking abortions falls.
That speecch is mandated, yet SCOTUS barred California from mandating crisis pregancy centers reporting to patients you cannot get an abortion here but instead call these numbers to schedule one
Lots of controversies outside the topic of the thread, but certainly examples of mandated speech and rulings to prevent mandated speech.
Also to note, that Purplix does warn users to assume the site has been compromised if the latest statement has expired.
That actually could be useful, by having a completely external company send a notification without action by the company receiving the warrant, it may be possible to circumvent the prohibition on alerting users.
deleted by creator
Passphrases only work in locales with 5a or similar protection, and either have to be managed by a single person or have the potential to be leaked.
Great for small businesses, but unworkable at the enterprise level.
But having a canary mechanism for smaller businesses is crucial, because they can’t afford to put a wall of lawyers between them and potential government overreach.
The canary is triggered through inaction, not action. The government would have to compel the target of the subpoena to keep updating the canary on schedule.